Configure AWS CLI
You need to provide the AWS access credential to do any kind of automation
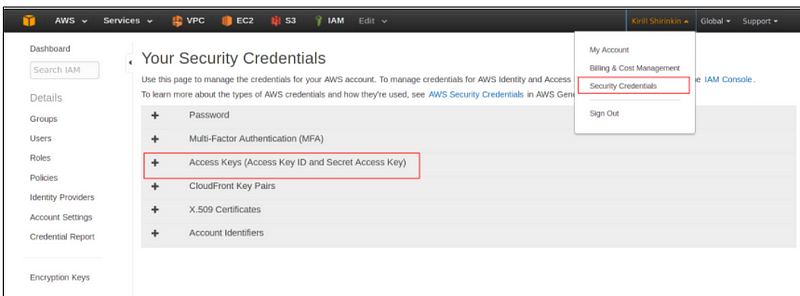
You can find the security credentials of any IAM user as shown below
You need python-pip on that machine to install awscli
yum install https://dl.fedoraproject.org/pub/epel/epel-release-latest-7.noarch.rpm
sudo yum install python-pip
sudo pip install awscli --upgrade pipRun the below command after logging to some user, for eg -ec2-user not as a root user
aws configure
Once you configured your keys using aws configure, everything is stored under
cd ~/.aws/ pwd /home/ec2-user/.aws cat credentials
By default, a default profile is created as show below
[default]
region=us-west-2
output=json
aws_access_key_id=
aws_secret_access_key=
Its best practice to create a profile and use that for any kind of automation as shown below. You can directly edit the file or run the below command to configure it
aws configure –profile profilename
[profile user2]
region=us-east-1
output=text
aws_access_key_id=
aws_secret_access_key=
You can delete your default configuration as whenever you run anything without providing profile name it will automatically take the default profile name
Configure AWS CLI for cross account
Suppose you have multiple accounts , one is where you put all your scripting code and other accounts where you want to create resources.
Steps:
- Create IAM role on sub accounts where resources needs to be created with Admin access and you to put the account number of your scripting account
- Create IAM role on your master account and assume the role.
- AWS CLI doesn’t work directly by just assume the role on your EC2 instance.
[default]
region = us-west-2
#credential of builduser on pipeline account
aws_access_key_id=accesskey
aws_secret_access_key=secretkey
[profile Kinesis]
role_arn = arn:aws:iam::accountnumber6:role/CrossAccountRole_Kinesis
region = us-west-2
source_profile = default
Click Here for other options to configure credentials for terraform.
NOTE: If your user has MFA enabled then that user is not able to use aws cli directly and you will get authentication error